The Four Phases
to
Implement effective
Counter Terrorism Mitigation
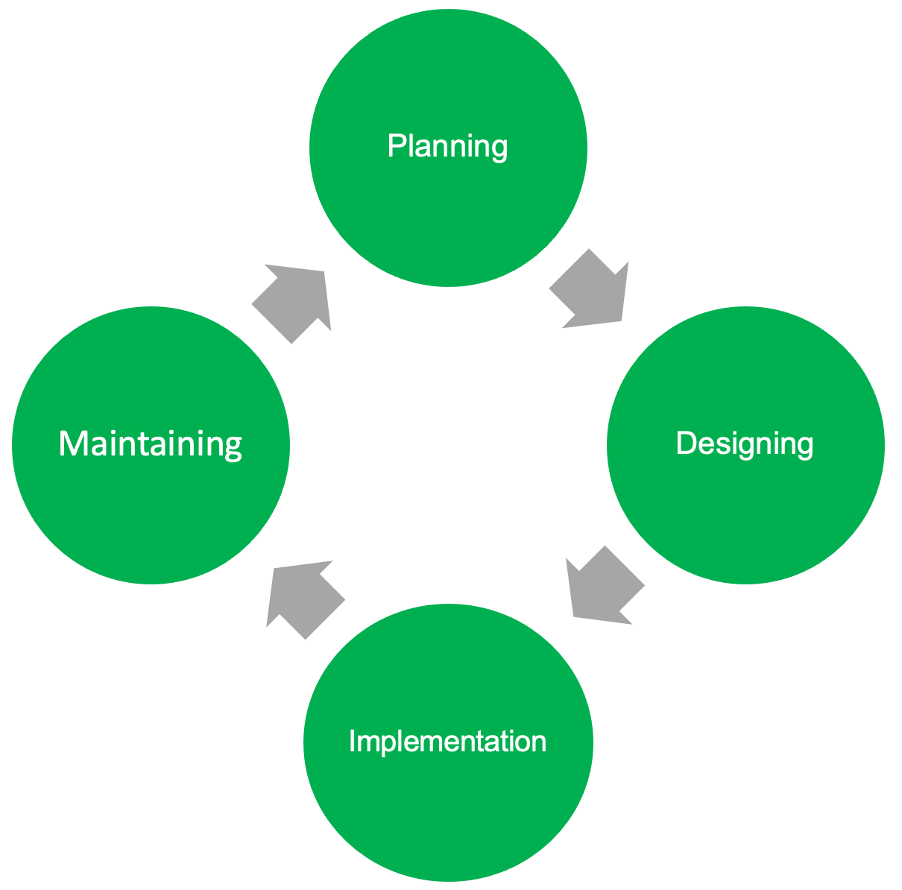
Key Features:
Systematic Approach: Learn to navigate through a structured four-phase process, which guides you from the initial planning stages to the robust maintenance of your security system. This approach ensures no element is overlooked and that security measures are seamlessly integrated into your organisation.
Counter Terrorism Focus: With an emphasis on counter terrorism, our eBook prepares you to address these critical threats directly. It equips your team with the knowledge and strategies necessary to design and implement effective counter measures.
Invest in Your Security
Securing your organisation is not just an operational necessity; it is a strategic imperative. Strategic Security System Design for Counter Terrorism & Hybrid Threats is an investment in future-proofing your assets against the most pressing threats of our time.
Equip your team with the knowledge to anticipate, prepare for, and neutralise risks effectively.
To view this content enter your membership login details.
Or, Click this link to gain access to all the premium resources for £49.50






